Download - Academy Publisher
Download - Academy Publisher
Download - Academy Publisher
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
in routing table. When search resources CAN uses greedy<br />
algorithm and send the messages to the neighbor node<br />
which is nearest to target according the routing table.<br />
Each node has O(d) neighbor nodes, and the hops of<br />
searching is O(dN 1/d )[14]. The topology of CAN is shown<br />
in figure 3.<br />
The biggest problem of DHT structure is that the<br />
mechanism of maintenance is too complex. In particular<br />
while there are nodes always join or quit the system, it<br />
becomes difficult to maintain. The other shortage of<br />
DHT is that it supports exact keywords search only. It<br />
can’t support the content of complex queries.<br />
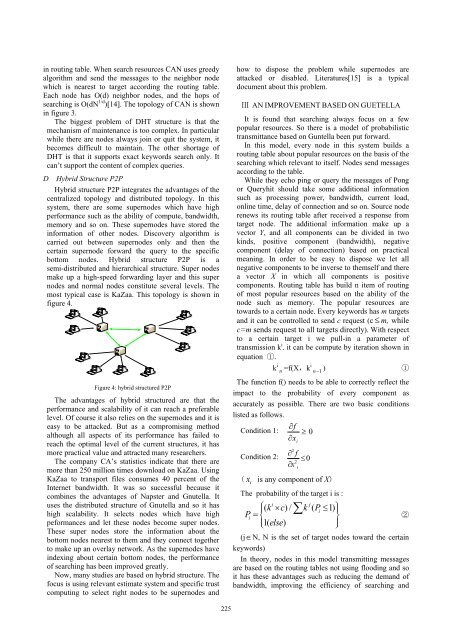
D Hybrid Structure P2P<br />
Hybrid structure P2P integrates the advantages of the<br />
centralized topology and distributed topology. In this<br />
system, there are some supernodes which have high<br />
performance such as the ability of compute, bandwidth,<br />
memory and so on. These supernodes have stored the<br />
information of other nodes. Discovery algorithm is<br />
carried out between supernodes only and then the<br />
certain supernode forward the query to the specific<br />
bottom nodes. Hybrid structure P2P is a<br />
semi-distributed and hierarchical structure. Super nodes<br />
make up a high-speed forwarding layer and this super<br />
nodes and normal nodes constitute several levels. The<br />
most typical case is KaZaa. This topology is shown in<br />
figure 4.<br />
Figure 4: hybrid structured P2P<br />
The advantages of hybrid structured are that the<br />
performance and scalability of it can reach a preferable<br />
level. Of course it also relies on the supernodes and it is<br />
easy to be attacked. But as a compromising method<br />
although all aspects of its performance has failed to<br />
reach the optimal level of the current structures, it has<br />
more practical value and attracted many researchers.<br />
The company CA’s statistics indicate that there are<br />
more than 250 million times download on KaZaa. Using<br />
KaZaa to transport files consumes 40 percent of the<br />
Internet bandwidth. It was so successful because it<br />
combines the advantages of Napster and Gnutella. It<br />
uses the distributed structure of Gnutella and so it has<br />
high scalability. It selects nodes which have high<br />
peformances and let these nodes become super nodes.<br />
These super nodes store the information about the<br />
bottom nodes nearest to them and they connect together<br />
to make up an overlay network. As the supernodes have<br />
indexing about certain bottom nodes, the performance<br />
of searching has been improved greatly.<br />
Now, many studies are based on hybrid structure. The<br />
focus is using relevant estimate system and specific trust<br />
computing to select right nodes to be supernodes and<br />
how to dispose the problem while supernodes are<br />
attacked or disabled. Literatures[15] is a typical<br />
document about this problem.<br />
Ⅲ AN IMPROVEMENT BASED ON GUETELLA<br />
It is found that searching always focus on a few<br />
popular resources. So there is a model of probabilistic<br />
transmittance based on Guntella been put forward.<br />
In this model, every node in this system builds a<br />
routing table about popular resources on the basis of the<br />
searching which relevant to itself. Nodes send messages<br />
according to the table.<br />
While they echo ping or query the messages of Pong<br />
or Queryhit should take some additional information<br />
such as processing power, bandwidth, current load,<br />
online time, delay of connection and so on. Source node<br />
renews its routing table after received a response from<br />
target node. The additional information make up a<br />
vector Y, and all components can be divided in two<br />
kinds, positive component (bandwidth), negative<br />
component (delay of connection) based on practical<br />
meaning. In order to be easy to dispose we let all<br />
negative components to be inverse to themself and there<br />
a vector X in which all components is positive<br />
components. Routing table has build n item of routing<br />
of most popular resources based on the ability of the<br />
node such as memory. The popular resources are<br />
towards to a certain node. Every keywords has m targets<br />
and it can be controlled to send c request (c ≤ m, while<br />
c=m sends request to all targets directly). With respect<br />
to a certain target i we pull-in a parameter of<br />
transmission k i . it can be compute by iteration shown in<br />
equation 1.<br />
k i n =f(X,ki n −1<br />
) 1<br />
The function f() needs to be able to correctly reflect the<br />
impact to the probability of every component as<br />
accurately as possible. There are two basic conditions<br />
listed as follows.<br />
∂f<br />
Condition 1: ≥ 0<br />
∂xi<br />
2<br />
Condition 2:<br />
∂ f<br />
≤0<br />
2<br />
∂x<br />
i<br />
( x i<br />
is any component of X)<br />
The probability of the target i is :<br />
i<br />
j<br />
⎧⎪<br />
( k × c)/ ∑ k ( Pi<br />
≤1)<br />
⎫⎪<br />
2<br />
Pi<br />
= ⎨ ⎬<br />
⎩⎪<br />
1( else)<br />
⎭⎪<br />
(j∈ N, N is the set of target nodes toward the certain<br />
keywords)<br />
In theory, nodes in this model transmitting messages<br />
are based on the routing tables not using flooding and so<br />
it has these advantages such as reducing the demand of<br />
bandwidth, improving the efficiency of searching and<br />
225