Download - Academy Publisher
Download - Academy Publisher
Download - Academy Publisher
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
focused mainly on rule-based forms of expression. The<br />
following are examples of some well-known policy<br />
language:<br />
1) PDL (Policy Description Language) is a Bell<br />
Labs-developed event-based language [6]. They use<br />
"event - condition - behavior" rules of the form to define<br />
a policy. PDL’s syntax is simple, with clear semantics<br />
and can express a strong sexual, However, PDL does not<br />
support Access Control Policy, and does not support the<br />
roles of complex strategies.<br />
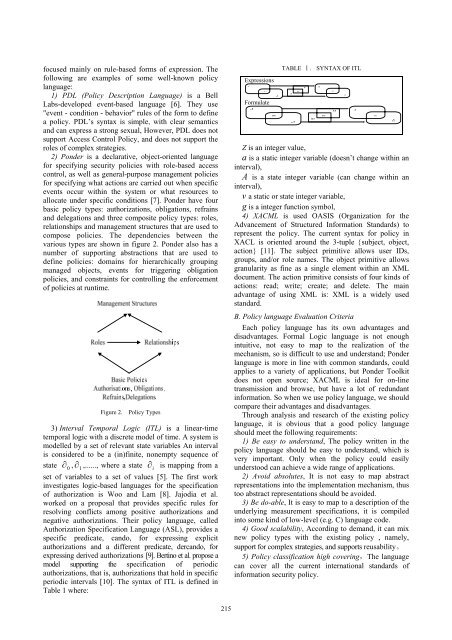
2) Ponder is a declarative, object-oriented language<br />
for specifying security policies with role-based access<br />
control, as well as general-purpose management policies<br />
for specifying what actions are carried out when specific<br />
events occur within the system or what resources to<br />
allocate under specific conditions [7]. Ponder have four<br />
basic policy types: authorizations, obligations, refrains<br />
and delegations and three composite policy types: roles,<br />
relationships and management structures that are used to<br />
compose policies. The dependencies between the<br />
various types are shown in figure 2. Ponder also has a<br />
number of supporting abstractions that are used to<br />
define policies: domains for hierarchically grouping<br />
managed objects, events for triggering obligation<br />
policies, and constraints for controlling the enforcement<br />
of policies at runtime.<br />
Figure 2.<br />
Policy Types<br />
3) Interval Temporal Logic (ITL) is a linear-time<br />
temporal logic with a discrete model of time. A system is<br />
modelled by a set of relevant state variables An interval<br />
is considered to be a (in)finite, nonempty sequence of<br />
state ∂<br />
0<br />
, ∂<br />
1<br />
,......, where a state ∂<br />
i<br />
is mapping from a<br />
set of variables to a set of values [5]. The first work<br />
investigates logic-based languages for the specification<br />
of authorization is Woo and Lam [8]. Jajodia et al.<br />
worked on a proposal that provides specific rules for<br />
resolving conflicts among positive authorizations and<br />
negative authorizations. Their policy language, called<br />
Authorization Specification Language (ASL), provides a<br />
specific predicate, cando, for expressing explicit<br />
authorizations and a different predicate, dercando, for<br />
expressing derived authorizations [9]. Bertino et al. propose a<br />
model supporting the specification of periodic<br />
authorizations, that is, authorizations that hold in specific<br />
periodic intervals [10]. The syntax of ITL is defined in<br />
Table 1 where:<br />
Expressions<br />
Formulate<br />
TABLE Ⅰ. SYNTAX OF ITL<br />
Z is an integer value,<br />
a is a static integer variable (doesn’t change within an<br />
interval),<br />
A is a state integer variable (can change within an<br />
interval),<br />
v a static or state integer variable,<br />
g is a integer function symbol,<br />
4) XACML is used OASIS (Organization for the<br />
Advancement of Structured Information Standards) to<br />
represent the policy. The current syntax for policy in<br />
XACL is oriented around the 3-tuple {subject, object,<br />
action} [11]. The subject primitive allows user IDs,<br />
groups, and/or role names. The object primitive allows<br />
granularity as fine as a single element within an XML<br />
document. The action primitive consists of four kinds of<br />
actions: read; write; create; and delete. The main<br />
advantage of using XML is: XML is a widely used<br />
standard.<br />
B. Policy language Evaluation Criteria<br />
Each policy language has its own advantages and<br />
disadvantages. Formal Logic language is not enough<br />
intuitive, not easy to map to the realization of the<br />
mechanism, so is difficult to use and understand; Ponder<br />
language is more in line with common standards, could<br />
applies to a variety of applications, but Ponder Toolkit<br />
does not open source; XACML is ideal for on-line<br />
transmission and browse, but have a lot of redundant<br />
information. So when we use policy language, we should<br />
compare their advantages and disadvantages.<br />
Through analysis and research of the existing policy<br />
language, it is obvious that a good policy language<br />
should meet the following requirements:<br />
1) Be easy to understand, The policy written in the<br />
policy language should be easy to understand, which is<br />
very important. Only when the policy could easily<br />
understood can achieve a wide range of applications.<br />
2) Avoid absolutes, It is not easy to map abstract<br />
representations into the implementation mechanism, thus<br />
too abstract representations should be avoided.<br />
3) Be do-able, It is easy to map to a description of the<br />
underlying measurement specifications, it is compiled<br />
into some kind of low-level (e.g. C) language code.<br />
4) Good scalability, According to demand, it can mix<br />
new policy types with the existing policy , namely,<br />
support for complex strategies, and supports reusability。<br />
5) Policy classification high covering,The language<br />
can cover all the current international standards of<br />
information security policy.<br />
215