Download - Academy Publisher
Download - Academy Publisher
Download - Academy Publisher
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
The QoE i (T i ) is the ith user’s experience of the service<br />
quality in a period of time T i, The u i (t) is the average<br />
user’s service utility value measured K times in this<br />
period of time T i . The b ij is the user’s allocated broadband<br />
value of the service measured jth time in this period of<br />
time T i.<br />
4) Utility-policy Description.<br />
After the preceding analysis, we can arrive at the<br />
utility policy which describes the network performance<br />
assessment model. Specific example is shown in Figure 5.<br />
Figure 5 Example of Utility Policy.<br />
D. Action-policy Generation<br />
The action policy which is finally deployed and<br />
executed in the mobile network equipment, is divided into<br />
two categories: Resource allocation policy, which is<br />
generated automatically by the "dynamic policy<br />
generation module" according to predicating information<br />
and has been done a thorough study by project team<br />
members [10] ; the specific action policy set which are<br />
transformed from the high-level abstraction strategy.<br />
These policies work together to achieve the objective<br />
described by goal policy and mainly include:<br />
• Security Authorization Policy, completing<br />
verification whether the user calling to access the<br />
wireless cell is legal or not;<br />
• QoS Configuration Policy, being configured in the<br />
equipments that support QoS parameter<br />
configuration at the bottom level, carrying out data<br />
collection for the "network resource monitoring<br />
module", and completing autonomic management<br />
system’s monitoring functions;<br />
• Admission Control Policy, enforcing the accessing<br />
or switching process when the user calls for getting<br />
the required resources for example bandwidth<br />
through the dynamic policy;<br />
• Resource Adaptation Policy .When the system<br />
resources are inadequate, the dynamic policy<br />
optimization mechanism produces the resource<br />
adaptation policy to adjust the accessed user<br />
resource allocation, for example, to extrude the<br />
bandwidth of the elastic services or the lower<br />
degrade user service.<br />
IV. EXPERIMENT AND SIMULATION<br />
Suppose the total accessed channel capacity of the<br />
wireless cell is 10Mbps, the overall average arrival rate of<br />
handoff call and new call is in line with the Poisson<br />
distribution whose parameter is λ, and the service mean<br />
duration meets the negative exponential distribution<br />
whose parameter is 1/μ=120s. The resource allocation and<br />
access control of the new call and handoff call are<br />
enforced under the PBMRAM framework.<br />
System supports four types of service, the property is<br />
shown in Table 2, and the parameterεis set to 0.001.Two<br />
wireless resource allocation methods used to compare<br />
with PBMRAM are Utility Maximizing Allocation (UMA)<br />
and Fixed Reservation Allocation(FRA).<br />
Table 2 Analysis of Each Service’s Property Setting in the Model<br />
Service<br />
Type<br />
conversational<br />
class<br />
stream<br />
class<br />
interactive<br />
class<br />
background<br />
class<br />
Averag<br />
e<br />
Rate<br />
64<br />
Kbps<br />
256<br />
Kbps<br />
512<br />
Kbps<br />
64<br />
Kbps<br />
Average<br />
Duration<br />
B min B max Spref<br />
60s 64<br />
Kbps<br />
64<br />
Kbps<br />
300s 64 350<br />
Kbps Kbps<br />
120s 30 1<br />
Kbps Mbps<br />
30s 0 100<br />
Kbps<br />
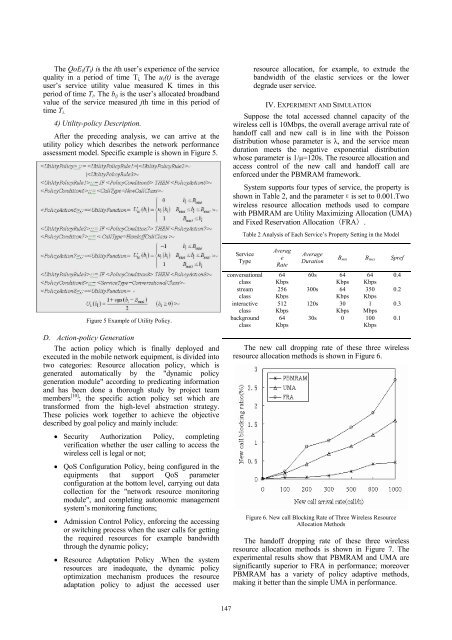
The new call dropping rate of these three wireless<br />
resource allocation methods is shown in Figure 6.<br />
Figure 6. New call Blocking Rate of Three Wireless Resource<br />
Allocation Methods<br />
The handoff dropping rate of these three wireless<br />
resource allocation methods is shown in Figure 7. The<br />
experimental results show that PBMRAM and UMA are<br />
significantly superior to FRA in performance; moreover<br />
PBMRAM has a variety of policy adaptive methods,<br />
making it better than the simple UMA in performance.<br />
0.4<br />
0.2<br />
0.3<br />
0.1<br />
147