Download - Academy Publisher
Download - Academy Publisher
Download - Academy Publisher
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
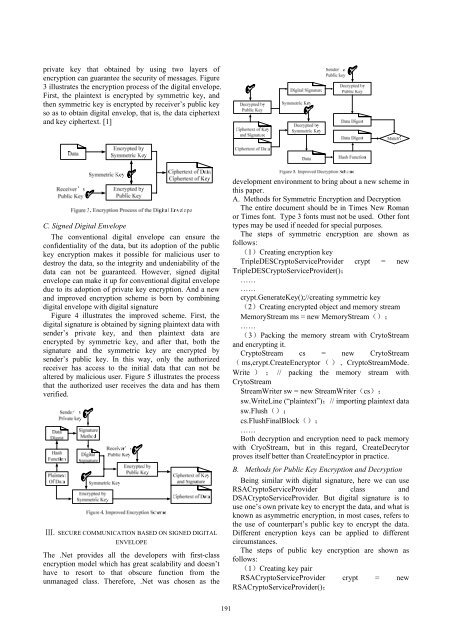
private key that obtained by using two layers of<br />
encryption can guarantee the security of messages. Figure<br />
3 illustrates the encryption process of the digital envelope.<br />
First, the plaintext is encrypted by symmetric key, and<br />
then symmetric key is encrypted by receiver’s public key<br />
so as to obtain digital envelop, that is, the data ciphertext<br />
and key ciphertext. [1]<br />
C. Signed Digital Envelope<br />
The conventional digital envelope can ensure the<br />
confidentiality of the data, but its adoption of the public<br />
key encryption makes it possible for malicious user to<br />
destroy the data, so the integrity and undeniability of the<br />
data can not be guaranteed. However, signed digital<br />
envelope can make it up for conventional digital envelope<br />
due to its adoption of private key encryption. And a new<br />
and improved encryption scheme is born by combining<br />
digital envelope with digital signature<br />
Figure 4 illustrates the improved scheme. First, the<br />
digital signature is obtained by signing plaintext data with<br />
sender’s private key, and then plaintext data are<br />
encrypted by symmetric key, and after that, both the<br />
signature and the symmetric key are encrypted by<br />
sender’s public key. In this way, only the authorized<br />
receiver has access to the initial data that can not be<br />
altered by malicious user. Figure 5 illustrates the process<br />
that the authorized user receives the data and has them<br />
verified.<br />
Ⅲ. SECURE COMMUNICATION BASED ON SIGNED DIGITAL<br />
ENVELOPE<br />
The .Net provides all the developers with first-class<br />
encryption model which has great scalability and doesn’t<br />
have to resort to that obscure function from the<br />
unmanaged class. Therefore, .Net was chosen as the<br />
development environment to bring about a new scheme in<br />
this paper.<br />
A. Methods for Symmetric Encryption and Decryption<br />
The entire document should be in Times New Roman<br />
or Times font. Type 3 fonts must not be used. Other font<br />
types may be used if needed for special purposes.<br />
The steps of symmetric encryption are shown as<br />
follows:<br />
(1)Creating encryption key<br />
TripleDESCryptoServiceProvider crypt = new<br />
TripleDESCryptoServiceProvider();<br />
……<br />
……<br />
crypt.GenerateKey();//creating symmetric key<br />
(2)Creating encrypted object and memory stream<br />
MemoryStream ms = new MemoryStream();<br />
……<br />
(3)Packing the memory stream with CrytoStream<br />
and encrypting it.<br />
CryptoStream cs = new CrytoStream<br />
( ms,crypt.CreateEncryptor (), CryptoStreamMode.<br />
Write ) ; // packing the memory stream with<br />
CrytoStream<br />
StreamWriter sw = new StreamWriter(cs);<br />
sw.WriteLine (“plaintext”);// importing plaintext data<br />
sw.Flush();<br />
cs.FlushFinalBlock();<br />
……<br />
Both decryption and encryption need to pack memory<br />
with CryoStream, but in this regard, CreateDecrytor<br />
proves itself better than CreateEncyptor in practice.<br />
B. Methods for Public Key Encryption and Decryption<br />
Being similar with digital signature, here we can use<br />
RSACryptoServiceProvider class and<br />
DSACryptoServiceProvider. But digital signature is to<br />
use one’s own private key to encrypt the data, and what is<br />
known as asymmetric encryption, in most cases, refers to<br />
the use of counterpart’s public key to encrypt the data.<br />
Different encryption keys can be applied to different<br />
circumstances.<br />
The steps of public key encryption are shown as<br />
follows:<br />
(1)Creating key pair<br />
RSACryptoServiceProvider crypt = new<br />
RSACryptoServiceProvider();<br />
191