Download - Academy Publisher
Download - Academy Publisher
Download - Academy Publisher
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
6) Opining source, the language definition itself is an<br />
open source, which can be modified to cater for the new<br />
changes.<br />
Ⅳ. SOLUTION TO THE CONFLICT<br />
In the policy-based applications, it is difficult to avoid<br />
conflicts between policies. So the tools to provide<br />
detection of conflict and conflict resolution approach are<br />
necessary. We discuses two kinds of conflict here:<br />
modality conflicts and application specific conflicts [12].<br />
A. modality conflicts<br />
The modality conflict is caused by inconsistencies in<br />
policy specification. When two or more policies use the<br />
same subject, behavior or goals that define the form of<br />
the opposite, then such conflicts occur. As shown in<br />
figure 3. it can be achieved by parsing policies to predict<br />
[13]. Because space is limited, we do not make a specific<br />
description.<br />
Figure 3.<br />
Form conflict<br />
B. application specific conflicts<br />
Application specific conflict refers to the conflict with<br />
the consistency of the elements, these elements that is<br />
related to the subject, objectives and standards of<br />
behavior and external. Such conflicts can not predict<br />
directly through the definition of policies, need to specify<br />
additional information that lead to conflict. The<br />
additional information is called meta-policy. There are<br />
two kinds of proposal of static and dynamic to resolve<br />
the semantic conflict by Application of meta-policy.<br />
Static proposal refers to the policies of conflict can not<br />
exist together in a system. Dynamic proposal is the<br />
policies of conflict can not be run at the same time to<br />
activate.<br />
Figure 4.<br />
FAM Framework<br />
2) Ponder policy deployment model. The framework is<br />
an extension of IETF policy management framework. It<br />
includes 3 supporting services: a domain service, a<br />
policy service, and an event service. The Policy Service<br />
acts as the interface to policy management, it stores<br />
compiled policy classes, creates and distributes new<br />
policy objects. The Domain Service manages a<br />
distributed hierarchy of domain objects and supports the<br />
efficient evaluation of subject and target sets at run-time.<br />
Each domain object holds references to its managed<br />
objects but also references to the policy objects that<br />
currently apply to the domain. The Event Service collects<br />
and composes events from the underlying systems and<br />
from the managed objects in the system, and forwards<br />
them to registered policy management agents triggering<br />
obligation policies. An overview of the policy<br />
deployment model is shown in figure 5.<br />
Ⅴ. POLICY FRAMEWORK<br />
A. Introduction<br />
SHAN [14] divided security policy framework into<br />
three categories in his dissertation: based on policy<br />
description language; based on security attributes and<br />
based on the unified model. The following are some<br />
well-known policy Framework:<br />
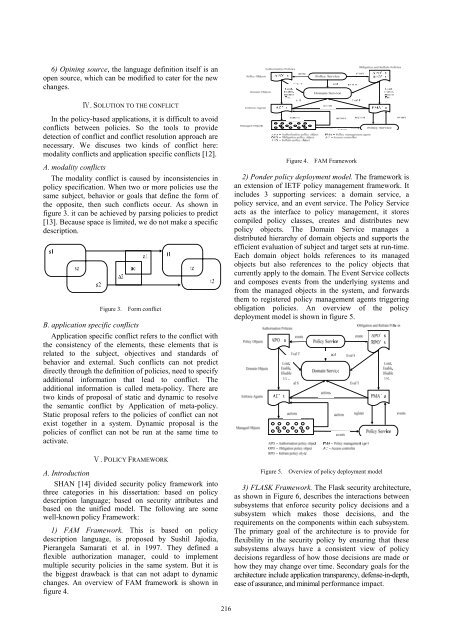
1) FAM Framework. This is based on policy<br />
description language, is proposed by Sushil Jajodia,<br />
Pierangela Samarati et al. in 1997. They defined a<br />
flexible authorization manager, could to implement<br />
multiple security policies in the same system. But it is<br />
the biggest drawback is that can not adapt to dynamic<br />
changes. An overview of FAM framework is shown in<br />
figure 4.<br />
Figure 5.<br />
Overview of policy deployment model<br />
3) FLASK Framework. The Flask security architecture,<br />
as shown in Figure 6, describes the interactions between<br />
subsystems that enforce security policy decisions and a<br />
subsystem which makes those decisions, and the<br />
requirements on the components within each subsystem.<br />
The primary goal of the architecture is to provide for<br />
flexibility in the security policy by ensuring that these<br />
subsystems always have a consistent view of policy<br />
decisions regardless of how those decisions are made or<br />
how they may change over time. Secondary goals for the<br />
architecture include application transparency, defense-in-depth,<br />
ease of assurance, and minimal performance impact.<br />
216