Child Pornography - Home | National Rapporteur on Trafficking in ...
Child Pornography - Home | National Rapporteur on Trafficking in ...
Child Pornography - Home | National Rapporteur on Trafficking in ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Introducti<strong>on</strong><br />
but also the extent to which any abusive c<strong>on</strong>text is taken <strong>in</strong>to account <strong>in</strong> other forms of <strong>in</strong>terventi<strong>on</strong> relat<strong>in</strong>g<br />
to sexual violence aga<strong>in</strong>st children, such as preventi<strong>on</strong>, identificati<strong>on</strong> and registrati<strong>on</strong> and care provisi<strong>on</strong><br />
for victims. With regard to certa<strong>in</strong> elements, it is not possible to make an explicit dist<strong>in</strong>cti<strong>on</strong> <strong>in</strong> relati<strong>on</strong><br />
to child pornography with<strong>in</strong> the broad c<strong>on</strong>text of sexual violence aga<strong>in</strong>st children, as we do not have<br />
that reference framework. We also assessed the extent to which policy and implementati<strong>on</strong> <strong>in</strong>corporate<br />
the complexity and <strong>in</strong> particular the variati<strong>on</strong> with<strong>in</strong> the phenomen<strong>on</strong> <strong>in</strong> <strong>in</strong>itiatives and actual acti<strong>on</strong>s.<br />
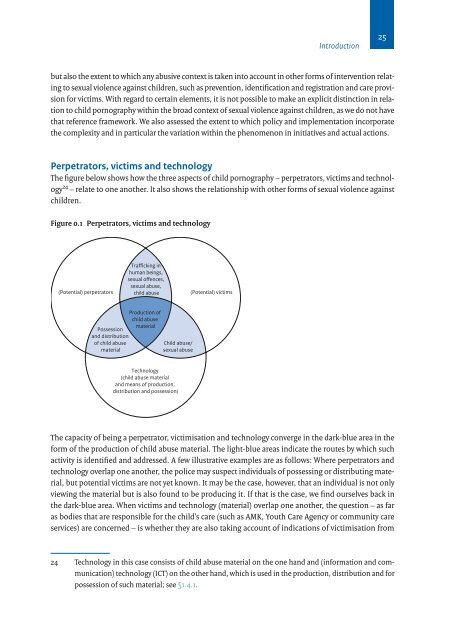
Perpetrators, victims and technology<br />
The figure below shows how the three aspects of child pornography – perpetrators, victims and technology<br />
24 – relate to <strong>on</strong>e another. It also shows the relati<strong>on</strong>ship with other forms of sexual violence aga<strong>in</strong>st<br />
children.<br />
Figure 0.1 Perpetrators, victims and technology<br />
(Potential) perpetrators<br />
Possessi<strong>on</strong><br />
and distributi<strong>on</strong><br />
of child abuse<br />
material<br />
Track<strong>in</strong>g <strong>in</strong><br />
human be<strong>in</strong>gs,<br />
sexual oences,<br />
sexual abuse,<br />
child abuse<br />
Producti<strong>on</strong> of<br />
child abuse<br />
material<br />
<str<strong>on</strong>g>Child</str<strong>on</strong>g> abuse/<br />
sexual abuse<br />
Technology<br />
(child abuse material<br />
and means of producti<strong>on</strong>,<br />
distributi<strong>on</strong> and possessi<strong>on</strong>)<br />
(Potential) victims<br />
The capacity of be<strong>in</strong>g a perpetrator, victimisati<strong>on</strong> and technology c<strong>on</strong>verge <strong>in</strong> the dark-blue area <strong>in</strong> the<br />
form of the producti<strong>on</strong> of child abuse material. The light-blue areas <strong>in</strong>dicate the routes by which such<br />
activity is identified and addressed. A few illustrative examples are as follows: Where perpetrators and<br />
technology overlap <strong>on</strong>e another, the police may suspect <strong>in</strong>dividuals of possess<strong>in</strong>g or distribut<strong>in</strong>g material,<br />
but potential victims are not yet known. It may be the case, however, that an <strong>in</strong>dividual is not <strong>on</strong>ly<br />
view<strong>in</strong>g the material but is also found to be produc<strong>in</strong>g it. If that is the case, we f<strong>in</strong>d ourselves back <strong>in</strong><br />
the dark-blue area. When victims and technology (material) overlap <strong>on</strong>e another, the questi<strong>on</strong> – as far<br />
as bodies that are resp<strong>on</strong>sible for the child’s care (such as AMK, Youth Care Agency or community care<br />
services) are c<strong>on</strong>cerned – is whether they are also tak<strong>in</strong>g account of <strong>in</strong>dicati<strong>on</strong>s of victimisati<strong>on</strong> from<br />
24 Technology <strong>in</strong> this case c<strong>on</strong>sists of child abuse material <strong>on</strong> the <strong>on</strong>e hand and (<strong>in</strong>formati<strong>on</strong> and communicati<strong>on</strong>)<br />
technology (ICT) <strong>on</strong> the other hand, which is used <strong>in</strong> the producti<strong>on</strong>, distributi<strong>on</strong> and for<br />
possessi<strong>on</strong> of such material; see §1.4.1.<br />
25