Child Pornography - Home | National Rapporteur on Trafficking in ...
Child Pornography - Home | National Rapporteur on Trafficking in ...
Child Pornography - Home | National Rapporteur on Trafficking in ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
The phenomen<strong>on</strong> of child pornography<br />
and justificati<strong>on</strong> for their behaviour <strong>on</strong>l<strong>in</strong>e. 292 In this way, the <strong>on</strong>l<strong>in</strong>e sub-culture fulfils a socio-emoti<strong>on</strong>al<br />
functi<strong>on</strong> as far as these <strong>in</strong>dividuals are c<strong>on</strong>cerned. It is a place where they are able to freely share their<br />
views. Aspects of their sexuality are discussed and (<strong>in</strong>formati<strong>on</strong> relat<strong>in</strong>g to) child abuse material, sexual<br />
preferences, fantasies and events are shared. Legislati<strong>on</strong> and regulati<strong>on</strong>s, and <strong>on</strong>l<strong>in</strong>e and offl<strong>in</strong>e security<br />
measures to rema<strong>in</strong> under the radar of the <strong>in</strong>vestigative authorities are also discussed. 293 Experienced collectors<br />
believe they are unassailable, judge the likelihood of arrest as low and have a low op<strong>in</strong>i<strong>on</strong> of the<br />
(calibre of ) <strong>in</strong>vestigative authorities. 294 It should be noted that some visitors to open Internet forums reject<br />
sex with children and the collecti<strong>on</strong> of child abuse material, as they recognise the harmful c<strong>on</strong>sequences<br />
for the child and therefore regard the abuse as be<strong>in</strong>g <strong>in</strong> c<strong>on</strong>flict with the actual love for the child. 295<br />
Summary us<strong>in</strong>g a pyramid model<br />
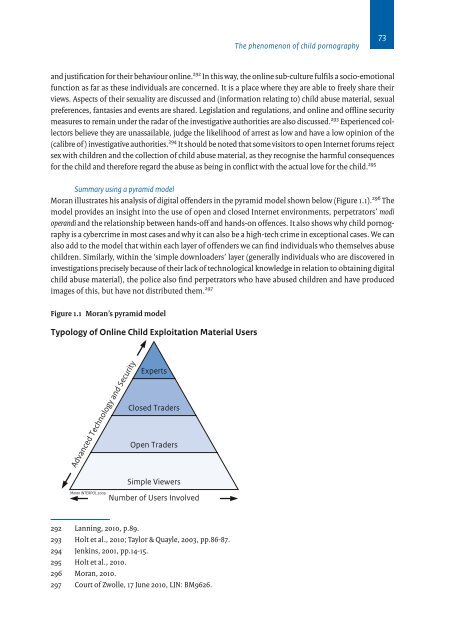
Moran illustrates his analysis of digital offenders <strong>in</strong> the pyramid model shown below (Figure 1.1). 296 The<br />
model provides an <strong>in</strong>sight <strong>in</strong>to the use of open and closed Internet envir<strong>on</strong>ments, perpetrators’ modi<br />
operandi and the relati<strong>on</strong>ship between hands-off and hands-<strong>on</strong> offences. It also shows why child pornography<br />
is a cybercrime <strong>in</strong> most cases and why it can also be a high-tech crime <strong>in</strong> excepti<strong>on</strong>al cases. We can<br />
also add to the model that with<strong>in</strong> each layer of offenders we can f<strong>in</strong>d <strong>in</strong>dividuals who themselves abuse<br />
children. Similarly, with<strong>in</strong> the ‘simple downloaders’ layer (generally <strong>in</strong>dividuals who are discovered <strong>in</strong><br />
<strong>in</strong>vestigati<strong>on</strong>s precisely because of their lack of technological knowledge <strong>in</strong> relati<strong>on</strong> to obta<strong>in</strong><strong>in</strong>g digital<br />
child abuse material), the police also f<strong>in</strong>d perpetrators who have abused children and have produced<br />
images of this, but have not distributed them. 297<br />
Figure 1.1 Moran’s pyramid model<br />
Typology of Onl<strong>in</strong>e <str<strong>on</strong>g>Child</str<strong>on</strong>g> Exploitati<strong>on</strong> Material Users<br />
Advanced Technology and Security<br />
Moran INTERPOL 2009<br />
Experts<br />
Closed Traders<br />
Open Traders<br />
Simple Viewers<br />
Number of Users Involved<br />
292 Lann<strong>in</strong>g, 2010, p.89.<br />
293 Holt et al., 2010; Taylor & Quayle, 2003, pp.86-87.<br />
294 Jenk<strong>in</strong>s, 2001, pp.14-15.<br />
295 Holt et al., 2010.<br />
296 Moran, 2010.<br />
297 Court of Zwolle, 17 June 2010, LJN: BM9626.<br />
73